The unix epoch is 1, January, 1970 apparently that's when all linux/unix computers were born. Windows however likes to think it's a lot older as its "born on date" is 1, January, 1601 it can be a little confusing having to switch between the 2. So I wrote a little script to aid in the process. Its fairly simple but ill go over it.
On linux the time is stored in seconds from midnight, so if for instance I had the number 1337133700 I could input that in python using time.ctime(1337133700) and I would get back 'Tue May 15 22:01:40 2012' .. which must have been one hell of a day.
Anyways on windows its a little different as linux uses a 32bit value and here we use a 64bit value, and rather than seconds its calculated using milliseconds since Jan,1,1601. To convert back and forth is actually really simple. We just take our unix time "1337133700" and add "11644473600" which is the "magic" number of milliseconds between 1601 and 1970. Then we simply multiply by 10000000.. so
(1337133700 + 11644473600) = 12981607300
(12981607300 * 10000000) = 129816073000000000
129816073000000000 = milliseconds since 1601
And that's really it, now most of the time you are not going to see that, however what you are going to see is a hex representation so to convert it simply use.
struct.pack("q", 129816073000000000)
and you will get \x00\x1a\x4d\xd5\x07\x33\xcd\x01
Now you might see something a little different if doing this in the shell but that's just python trying to convert hex into ascii for you... Anyways these are the 2 functions.
import time
import struct
def epoch_to_ms(ct = time.time()):
print("Input time since Epoch is: %s" % time.ctime(ct))
ms = (ct + 11644473600) * 10000000
print("Seconds since Jan, 1 1970: %f" % ct)
print("Millsec since Jan, 1 1601: %f" % ms)
pms = struct.pack("q", ms)
print("Little Endian Hex Value : %s" % '\\x' + '\\x'.join(x.encode('hex') for x in str(pms)))
def hexms_to_unix(ms_time):
ms = struct.unpack("q", ms_time)[0]
ct = (ms / 10000000) - 11644473600
print("Millsec since Jan, 1 1601: %f" % ms)
print("Seconds since Jan, 1 1970: %f" % ct)
print("Input time since Epoch is: %s" % time.ctime(ct))
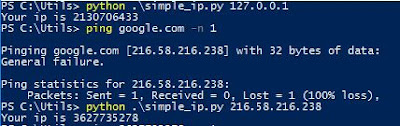
They both work as you can see here.
Now you might ask yourself, where am I ever going to see that.. well its simple really... ;)
A quick 2 things off subject...
1: I am working on getting another blog setup as blogger really bothers me.
2: The color always helps me, if you don't like it I'm sorry.